FrostGuard sent some thieves to Dr. Lovelace's residence. What exactly is it after?
Digital Forensics
Tags: Arsenal Image Mounter MFTECmd Timeline Explorer Registry Explorer IF015.001
Scenario Ava Lovelace—the world’s first programmer and head of the Council of Frost—had her home broken into. The thief seemed to have accessed her work computer, nothing else was tampered with. Can you find the motive for this breach?

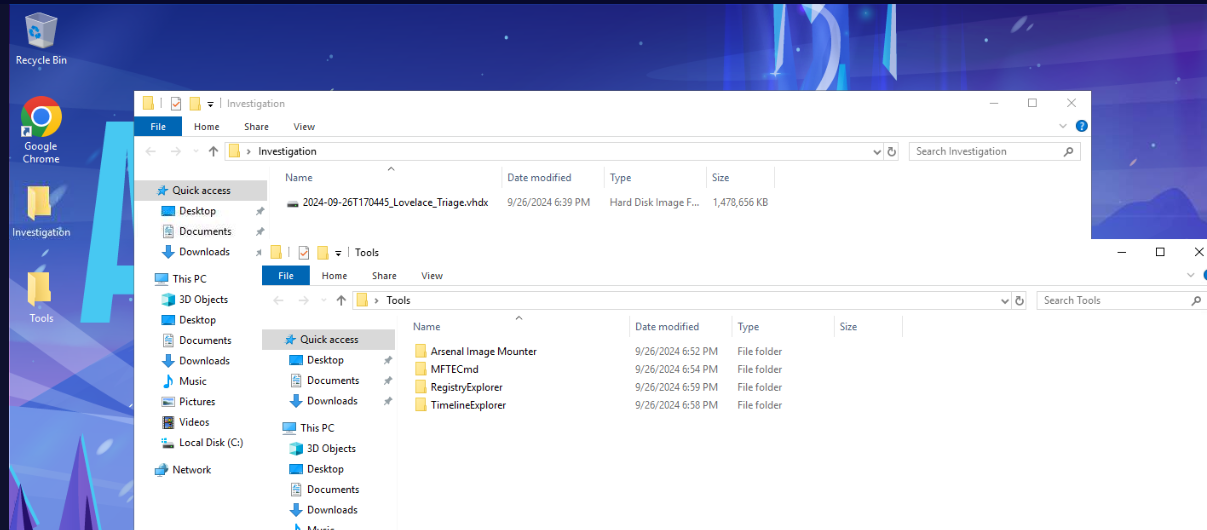
We are provide with vhdx disk image as a sole evidence on this investigation machine which we will have to mount it to discover more evidences.
There are 4 tools inside Tools folder on the Desktop which are
- Arsenal Image Mounter that could be used to mount disk image files
- MFTECmd from Eric Zimmerman's Tools that can be used to parse $MFT file (Master File Table)
we will have to mount this disk image with Arsenal Image Mounter first.
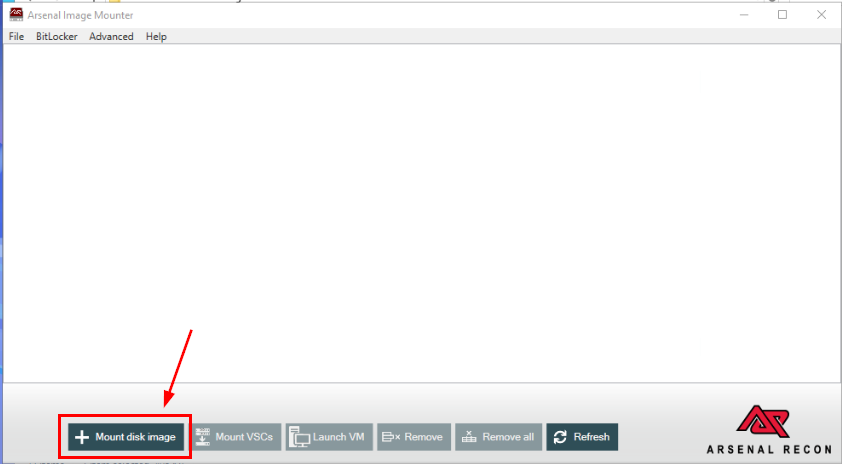
After open Arsenal Image Mounter program, click "Mount disk image"
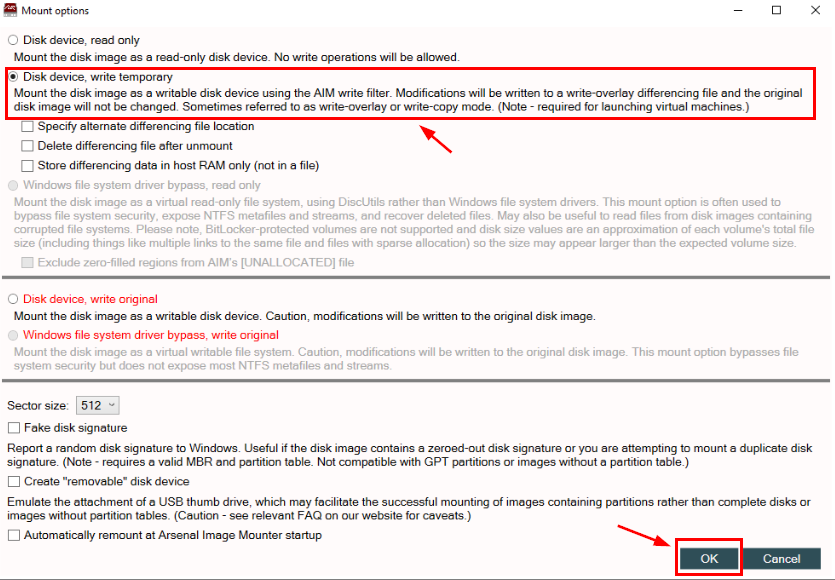
You will have "Disk device, write temporary" option since we do need this write permission to make it online, then we can proceed with "OK"
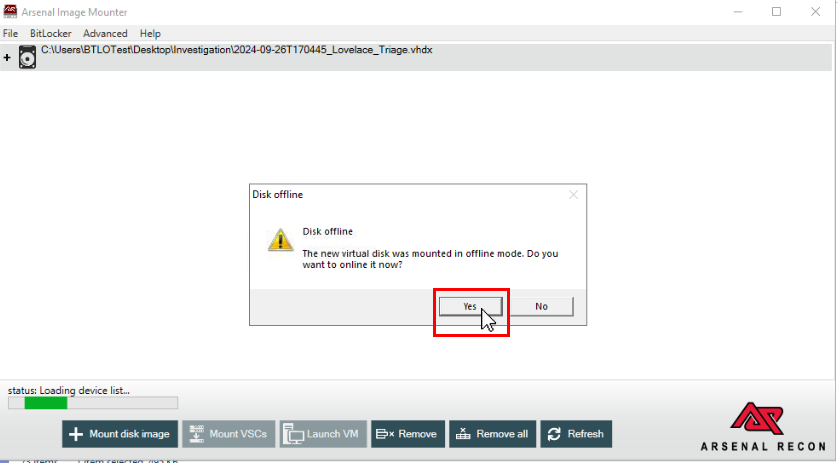
Then 2 pop-up will appear, just click "YES" twice to make this disk image online.
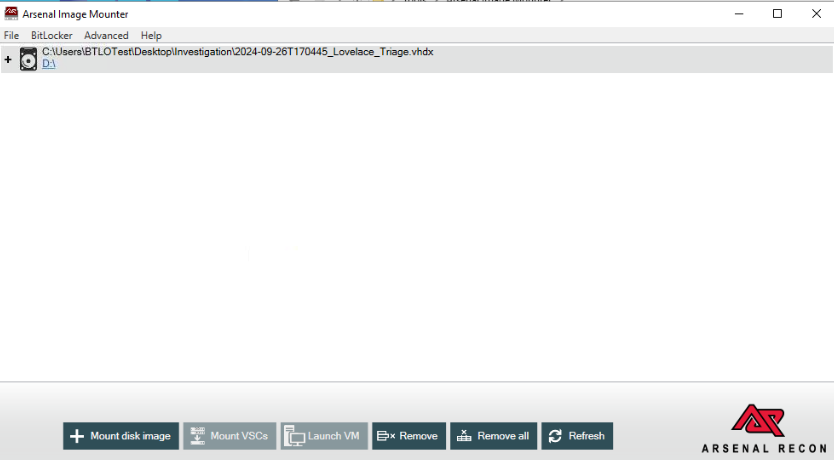
Now we should be able to browse this disk image on our D drive!
Q1) There is evidence of an anti-forensic tool during the break-in. What is the name of the software, what ITM ID corresponds with it, and when was it installed? (Format: Tool, AXXXX, YYYY-MM-DD HH:MM:SS UTC)
This disk image stores artifacts collected by KAPE then we can use Registry Explorer to browser SOFTWARE registry hive then locate to "Uninstall" registry key that holds path of each program that has uninstall executable and also have installation timestamp on each software.
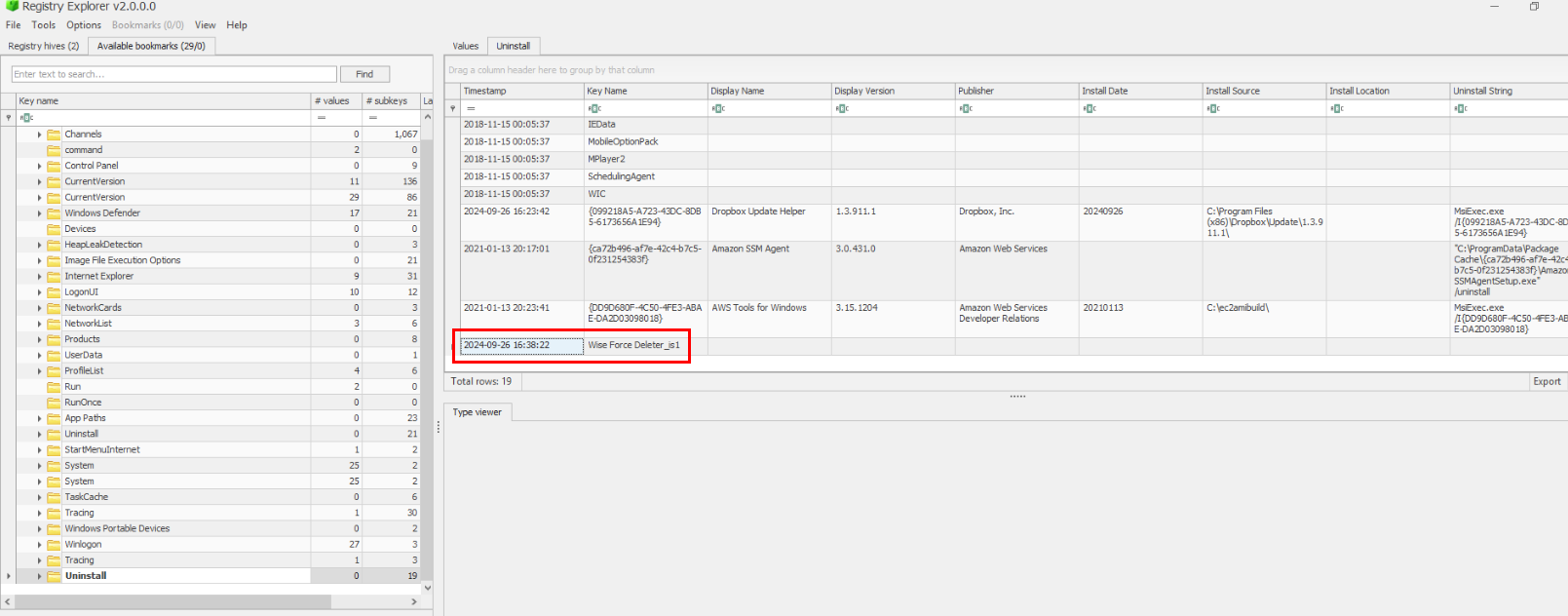
Which we can see Wise Force Deleter program was installed which can be used to easily and securely delete files.
 This action match AF015: File Deletion from Insider Threat Matrix
This action match AF015: File Deletion from Insider Threat Matrix
Answer
Wise Force Deleter, AF015, 2024-09-26 16:38:22 UTCQ2) It seems like multiple documents were accessed on Lovelace’s machine. What three projects, related to AI/Tech, have been accessed? Place in order of access time. (Format: Project Name, Project Name, Project Name)
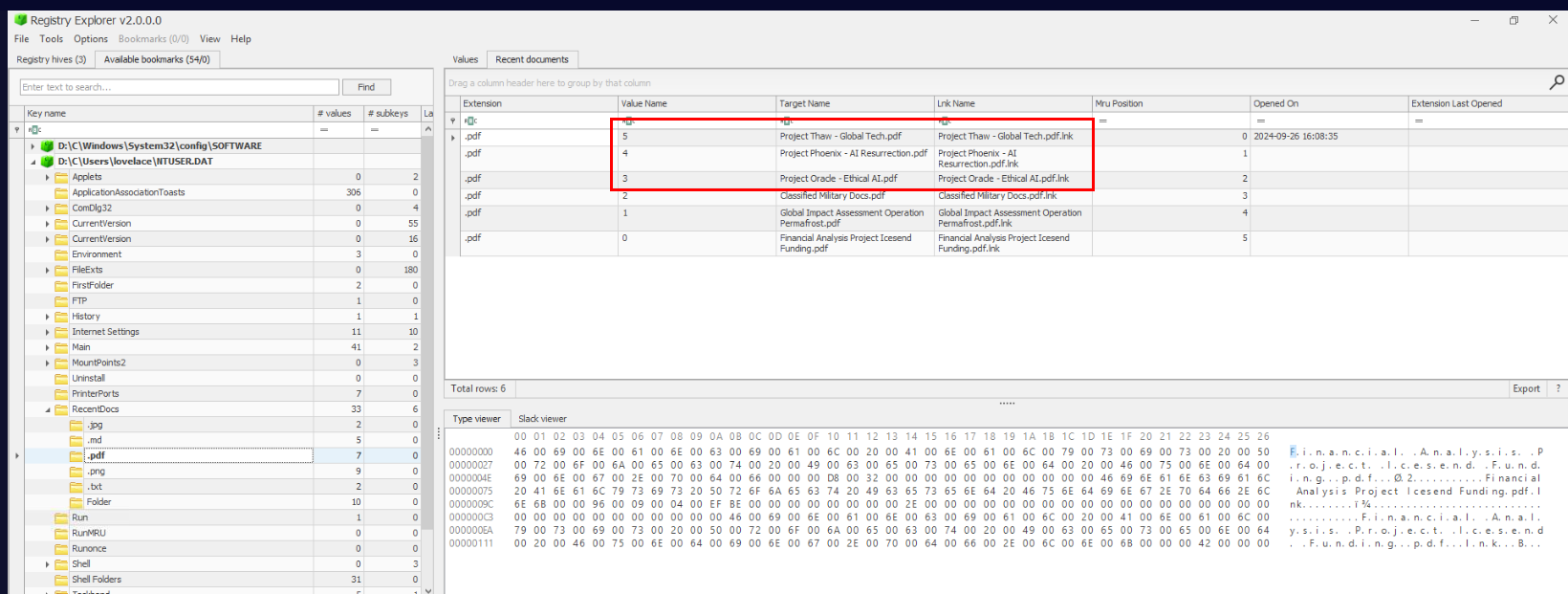
The next key I utilized for this question is "RecentDocs" key of lovelace user's NTUSER.dat hive which we can see that there are 3 pdf files that has "Project" in their name so to get order of access, we have to take a look at "Value Name" field which lower number mean access before higher number.
Answer
Project Oracle, Project Phoenix, Project ThawQ3) These documents were not local to Lovelace’s machine? From where did the hacker retrieve these confidential files? (Format: Location)
Next artifacts I was thinking of when asking about Origin of the file is Zone.Identifier so I used MFTECmd.exe to parse $MFT then use Timeline Explorer to open its result.
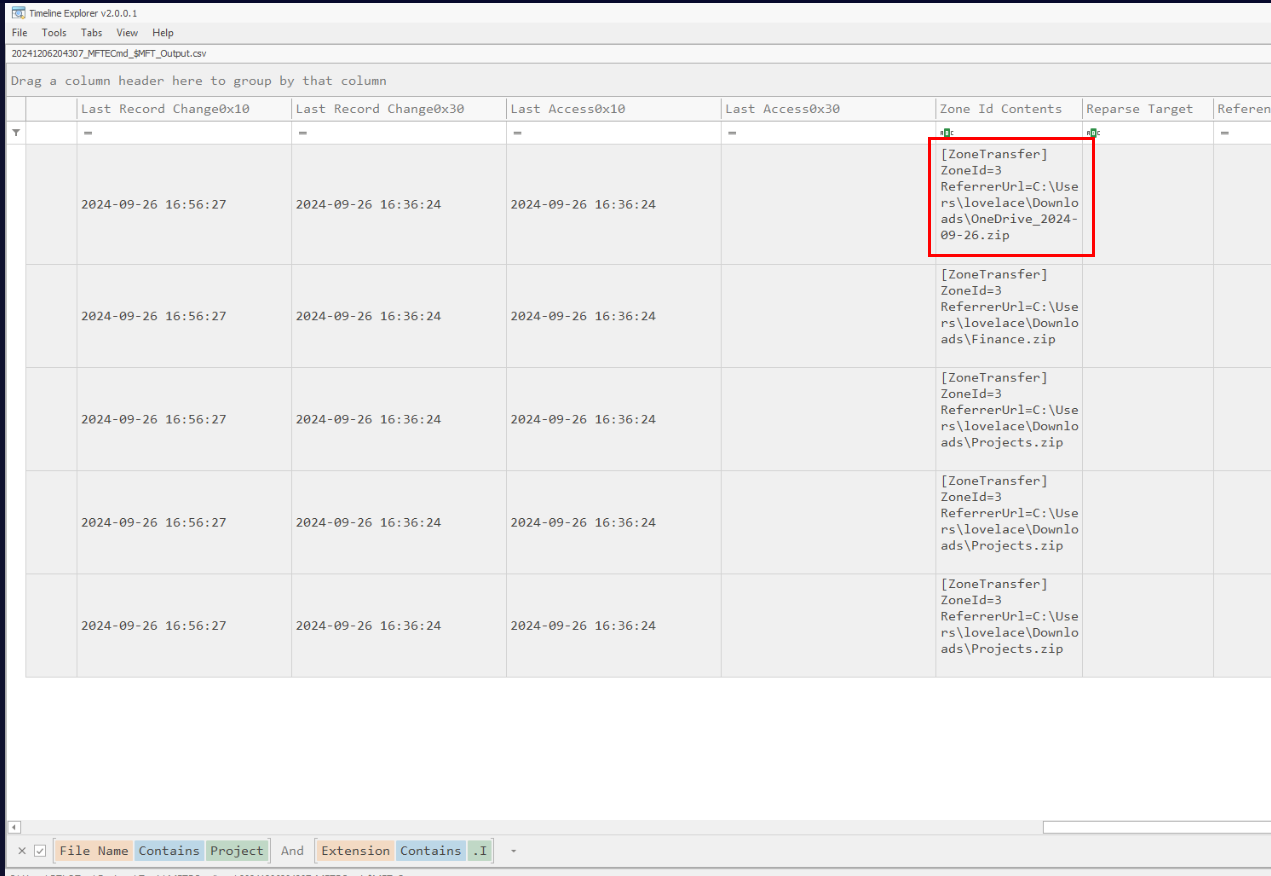
Then I filtered for "Zone.Identifier" of a filename that contains "Project" which we can see Zone ID Content of first record of this filter indicating it was downloaded from OneDrive
Answer
OnedriveQ4) The hacker did not brute force Lovelace’s computer, given the ‘Invalid Login Count.’ In respective order, can you provide the User ID, Total Login Count, and Last Password Change? (Format: XXXX, XX, YYYY-MM-DD HH:MM:SS UTC)
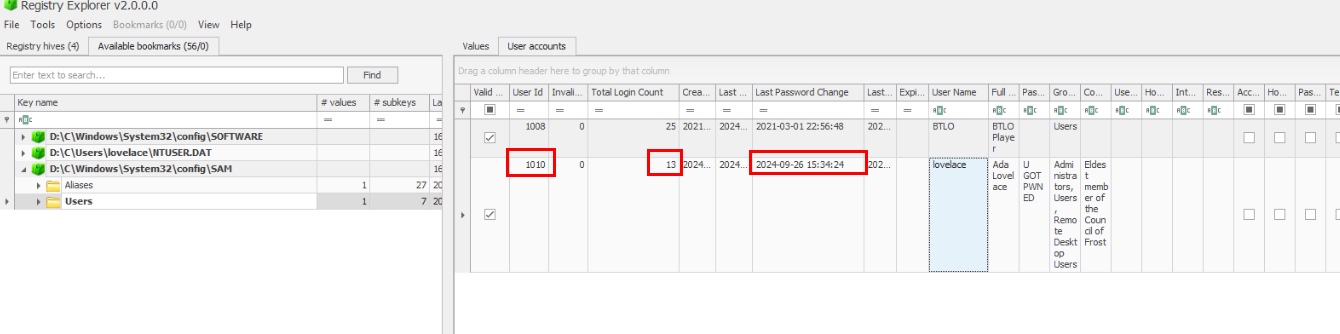
This time, we will have to use Registry Explorer to open SAM registry hive then navigate to Users key to get all answers needed for this question.
Answer
1010, 13, 2024-09-26 15:34:24 UTCQ5) Review the searches typed by the Ava Lovelace account. It looks like the hacker was looking for documents, but what was the first term executed? (Format: String)
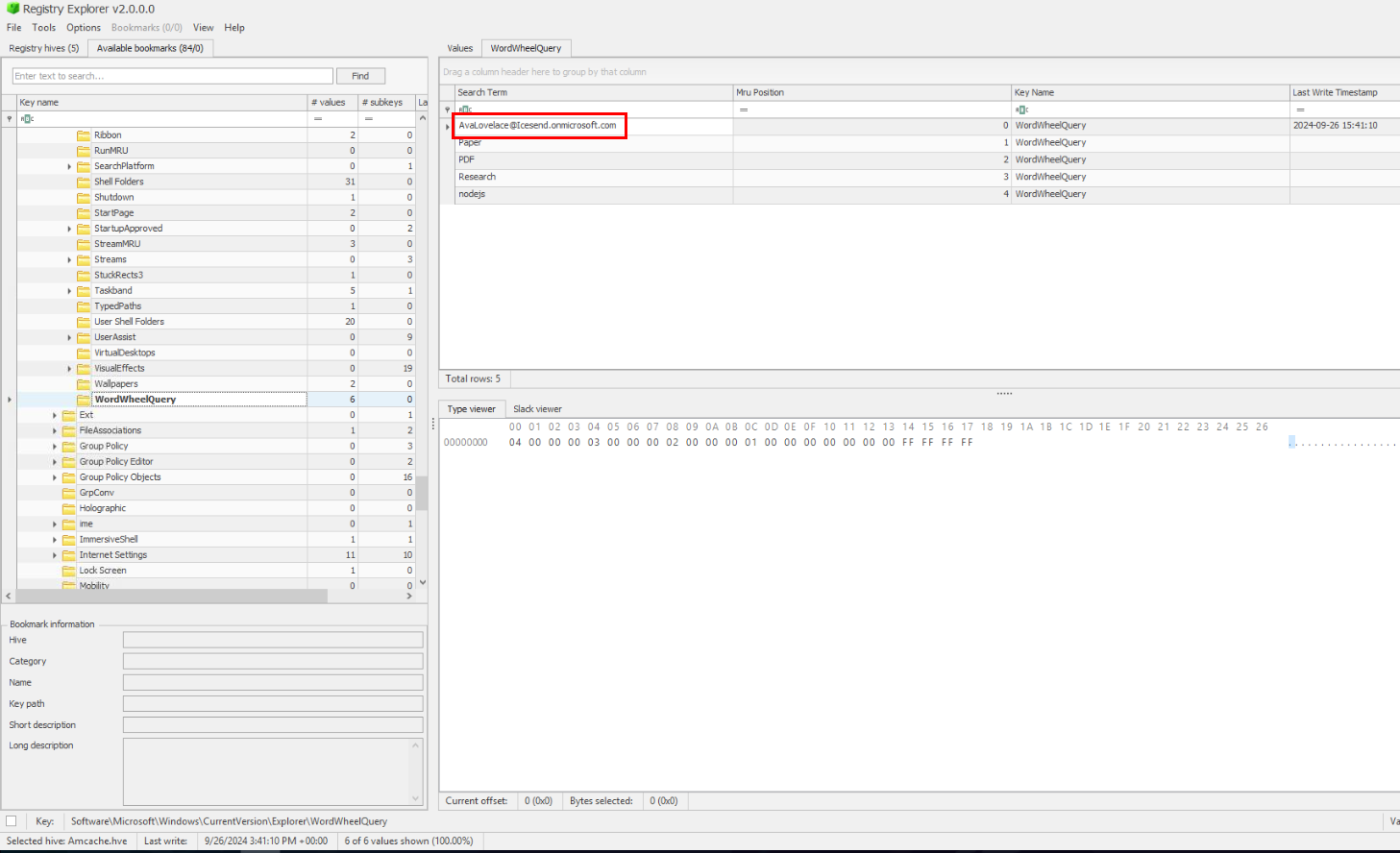
We can find search type history of each user from WordWheelQuery key reside their NTUSER.dat registry hive which we can see that the first search is the one with has the lowest Mru Position.
Answer
AvaLovelace@Icesend.onmicrosoft.comQ6) Given the string in the previous question, it looks like the hacker utilized another piece of information to access the resources online (Q3). What is the name of the file that has login credentials? (Format: File.txt)
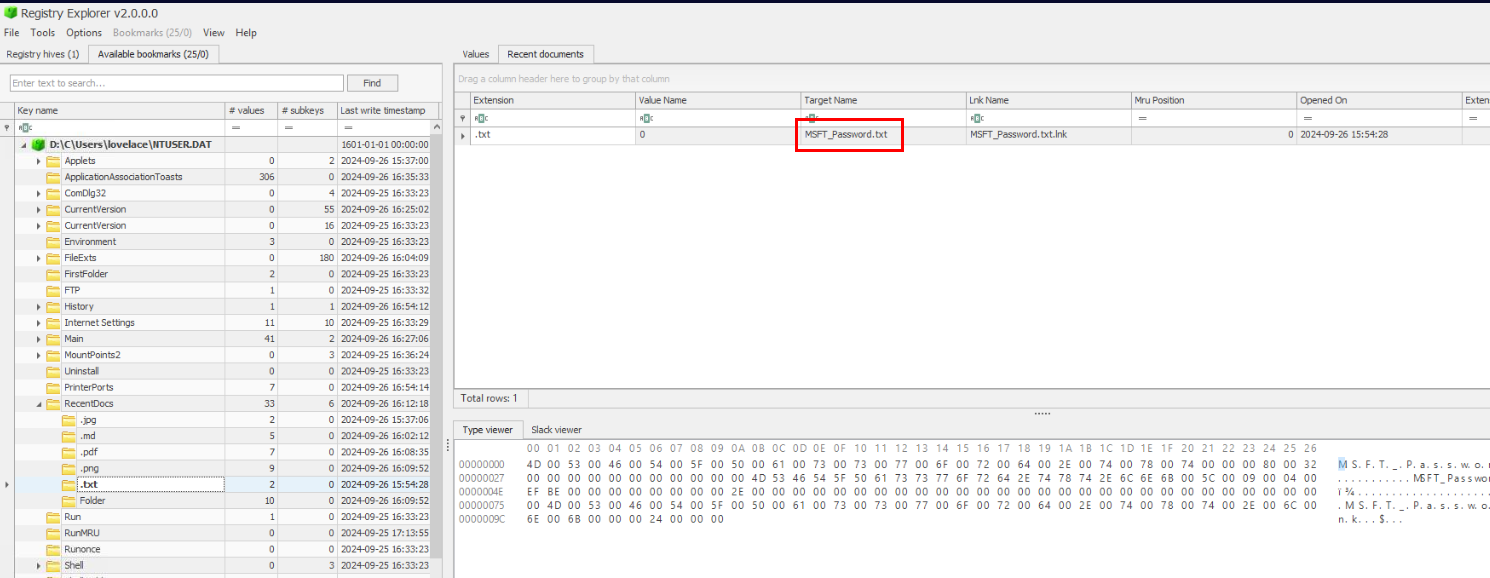
We can come back to RecentDocs registry key which we can see this text file was opened by lovelace user and it is the correct answer of this question.
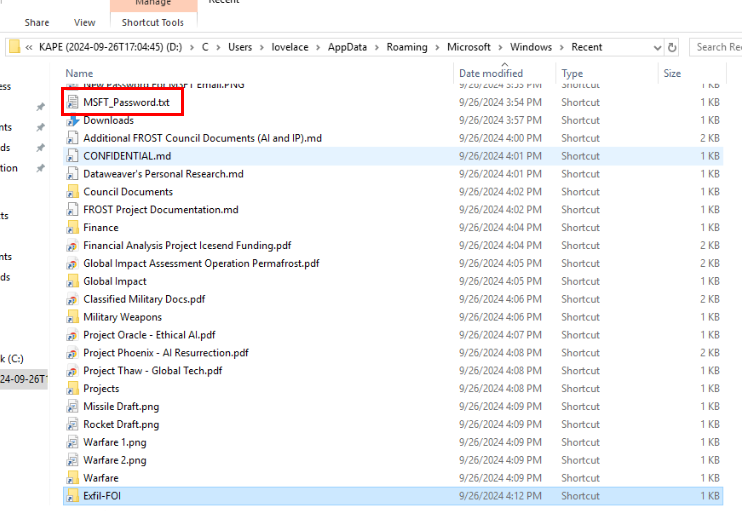
Alternatively, you can also find this on Recent folder of lovelace user right here.
Answer
MSFT_Password.txtQ7) The hacker changed the password for Lovelace’s account—the account in Q5. In what directory is the attacker storing this information and other stolen information, supposedly? (Format: Directory Name)
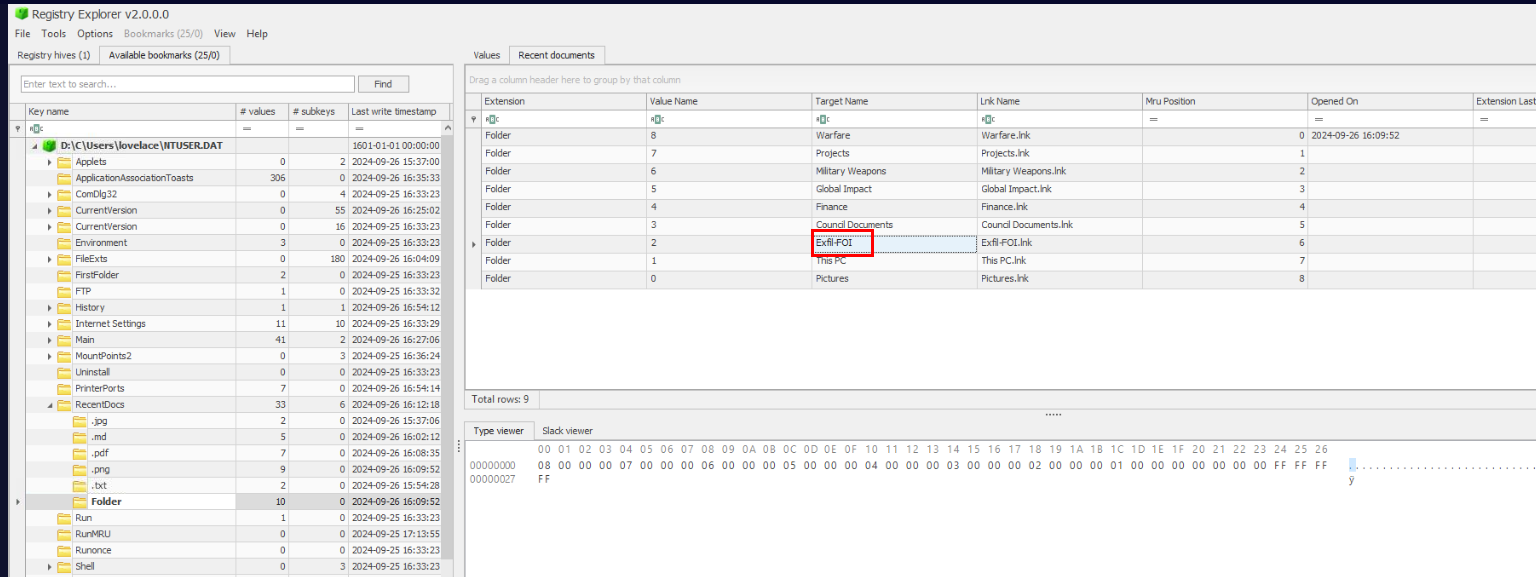
We're still at the RecentDocs registry key then we can see this weird folder with "Exfil" in its name which is a directory created to store information gathered on this machine.
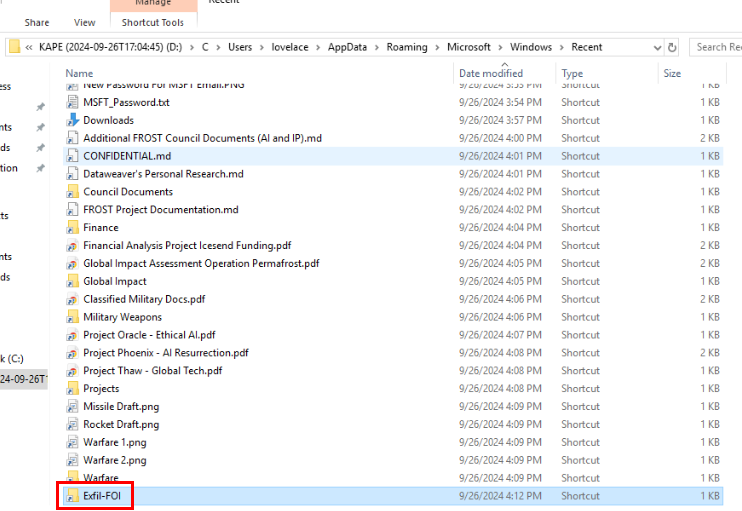
Alternatively, you can also find this on Recent folder of lovelace user right here.
Answer
Exfil-FOIQ8) Looks like the hacker tried to start an RDP session outbound to another system before settling for that Cloud Storage platform. What is the Execution Time of the program and the ITM ID that correlates with this event? (Format: YYYY-MM-DD HH:MM:SS UTC, MXXXX.XXX)
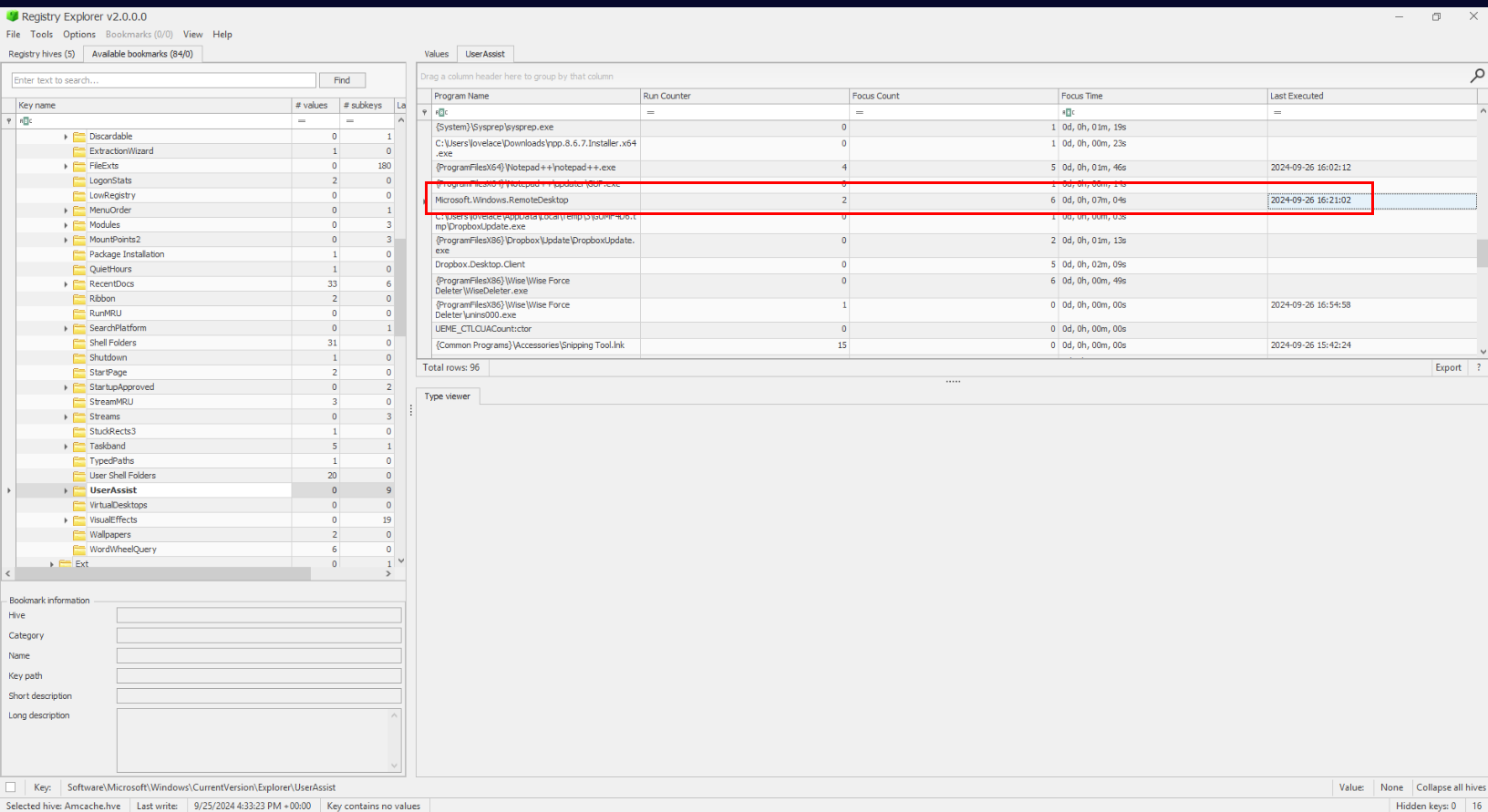
This time, I utilized UserAssist key from SOFTWARE registry hive to find the execution timestamp of RemoteDesktop program right here.
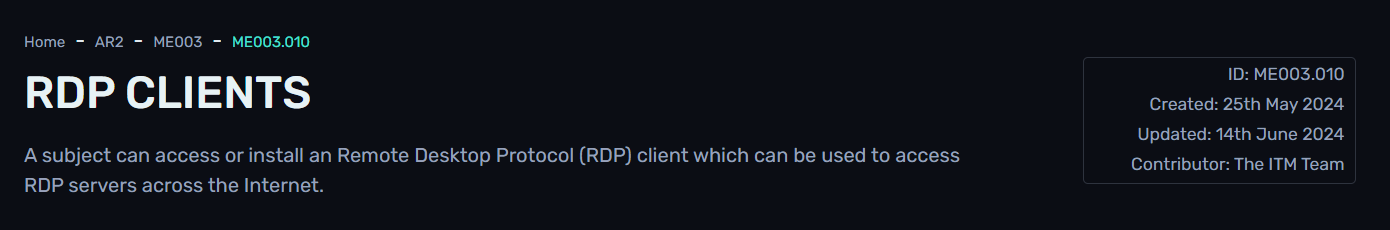
This match ME003.010: RDP Clients of Insider Threat Matrix
Answer
2024-09-26 16:21:02 UTC, ME003.010Q9) The hacker also shut down the system—after wiping the drive of the stolen files—to prevent RAM capture. What time did this occur? (Format: YYYY-MM-DD-SS HH:MM:SS UTC)
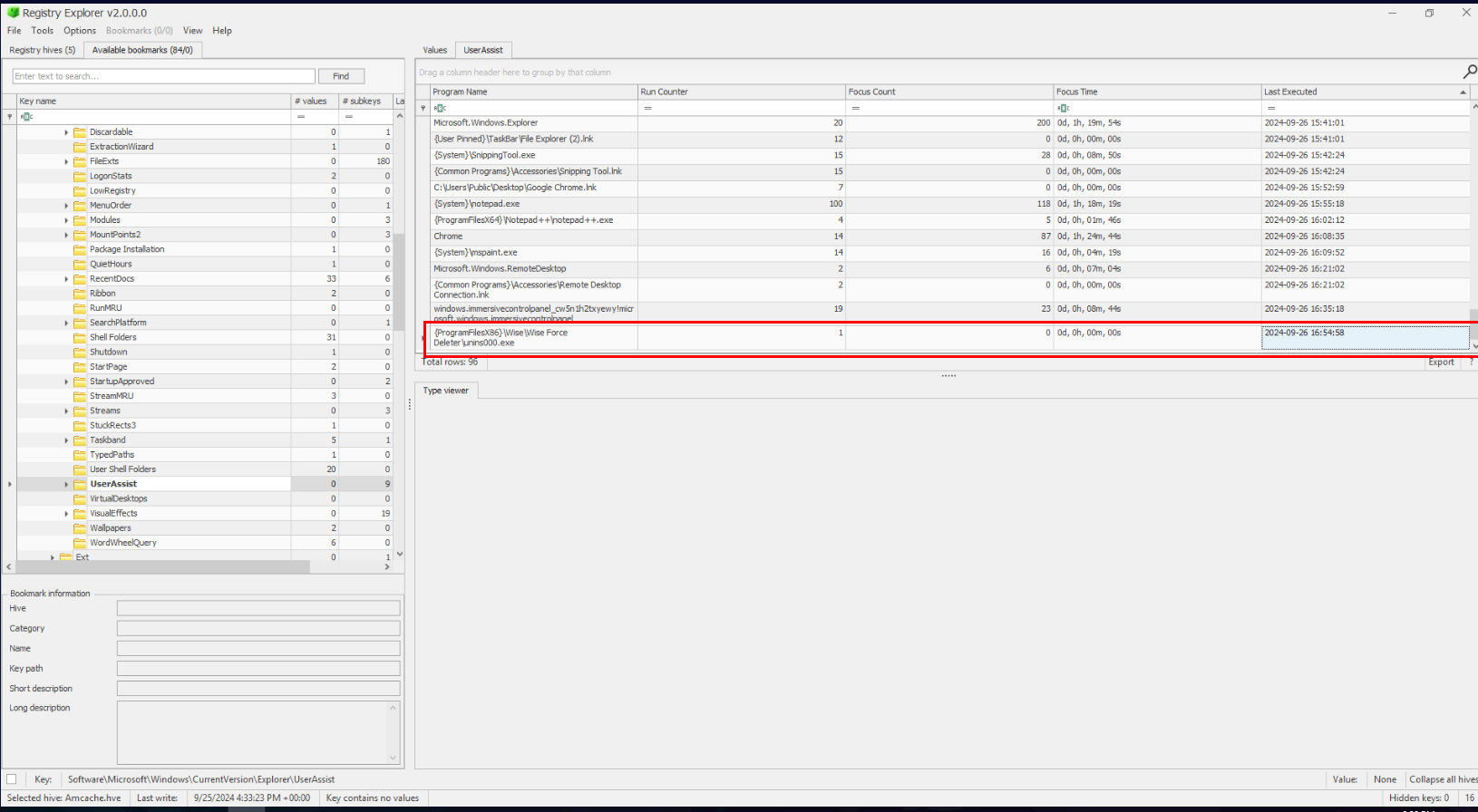
This question was a little bit mislead me into finding ShutDownTime registry key on this computer (which return incorrect answer of this question) so I went back to UserAssist key again and submit the timestamp of Wise Force Deleter Uninstallation executable file which got accepted as the correct answer. 🤔
Answer
2024-09-26 16:54:58 UTCQ10) The hacker utilized the built-in image capture tool: Snipping. How many times was it run, and what is the total focus time of the tool? This further proves the screenshots being placed in the directory (Q7). (Format: XX, XXm, XXs, MXXXX)
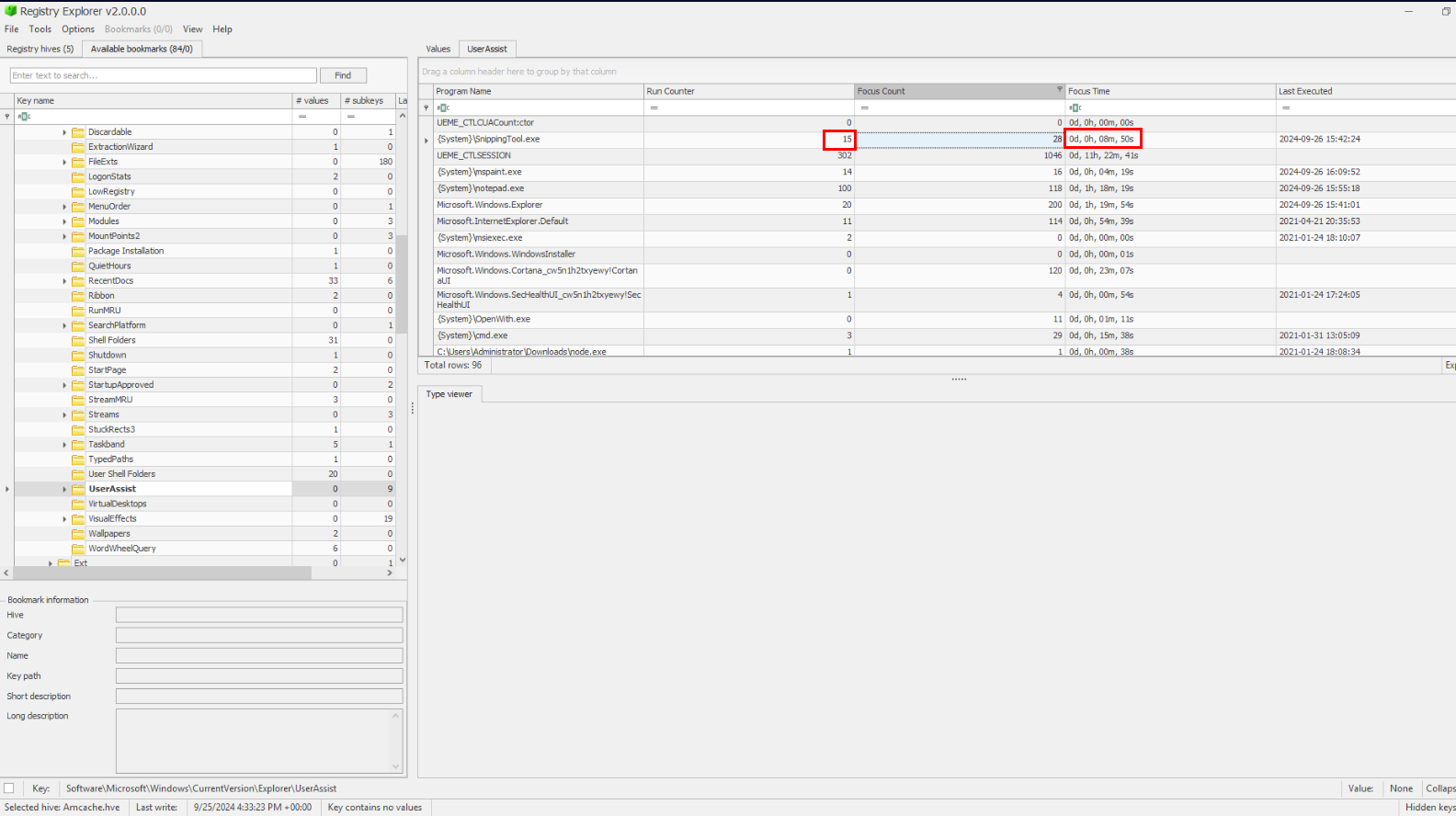
We know that UserAssist Key also stores run counter and focus time so we will just have to find SnippingTool.exe and retrieve both values right here
 This action match ME013: Media Capture of Insider Threat Matrix
This action match ME013: Media Capture of Insider Threat Matrix
Answer
15, 08m, 50s, ME013 https://blueteamlabs.online/achievement/share/52929/247
https://blueteamlabs.online/achievement/share/52929/247